Security researchers just traced Uiwix, a ransomware which is very similar to WannaCry but more dangerous than it

Now-a-days, the word "WannaCry" is very familiar to all of us. This ransomware exploited the vulnerabilities in Microsoft’s Windows operating system (except Windows 10) to hack more than 75,000 computers in more than 150 countries & counting last Friday. Microsoft has recently released the security patches for all versions of Winows including XP to prevent this ransomware. Also numerous security researchers are continuously working to develop a permanent solution. Although a temporary solution called "WannaCry KillSwitch" is already discovered by a british security researcher Marcus Hutchins. He slows down the spreads of WannaCry by registering a domain name "wannacry".
Heimdal Security, a cyber security software company has recently reported that another ransomware called Uiwix, has emerged, which is exploiting the vulnerabilities found in Windows SMB v1 and SMB v2. Wannacry is doing in the same method to spread.
Is Uiwix similar to WannaCry?
A group of security researchers has claimed that they have traced WannaCry in Uiwix. Yet, this does not mean that Uiwix & WannaCry are identical. Unfortunately, unlike WannaCry, Uiwix cannot be stopped from spreading just by registering a domain, the Killswitch of Wannacry. Hence, it's called Uiwix is far far more dangerous than WannaCry. Although even some temporary solutions for Wannacry exists, but, still there is no solution discovered for Uiwix.
How does Uiwix work ?
Uiwix works just like WannaCry. At first it attacks victim's PC, and encrypts important files on it. Then it demands a ransom $200 to get decrypt all the files seized by it. The ransom payment of $218 is demanded in bitcoins with the current exchange rate.
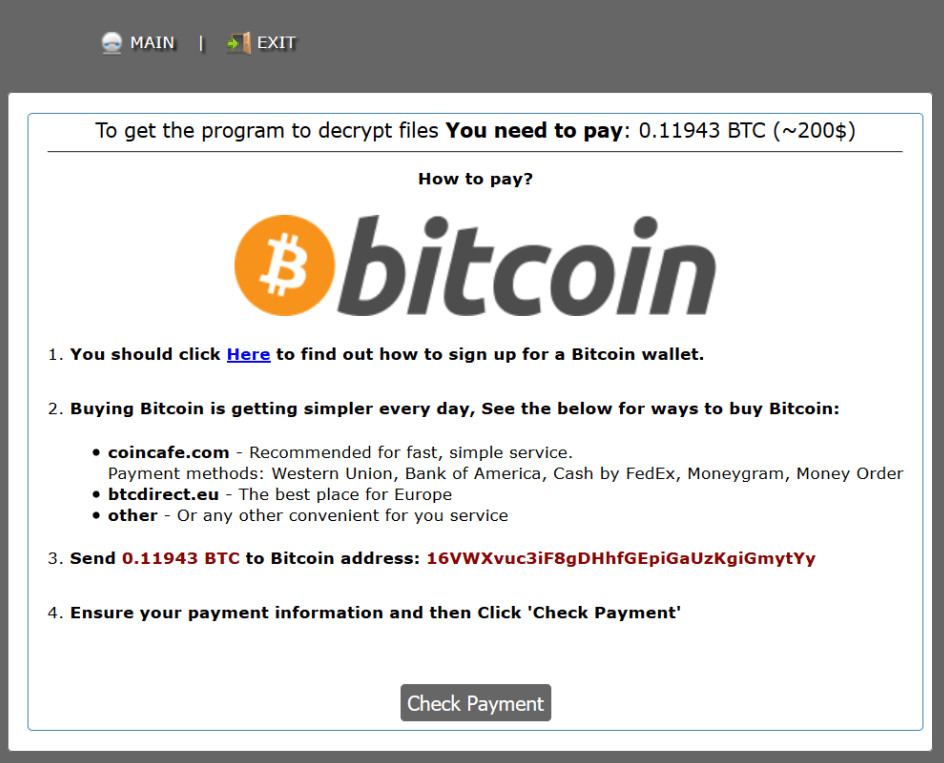
It is very astonishing to have two similar ransomware exploiting the same vulnerability to show up twice so rapidly. So, that it is said that vulnerabilities in Windows software have not been 100% fixed yet.
How to keep safe yourself from Uiwix ?
Since Uiwix cannot be stopped like WannaCry, the only way to contain the virus is to fix the vulnerability that appears to be present in Windows. According to Andra Zaharia, Heimdal Security (a cyber security software company) :
" Attackers are easily able to exploit these vulnerabilities in a network if it’s enabled because, even when the system uses SMB v2 or v3, if the attacker can downgrade the communication to SMB v1, he can exploit the system. This is where the man-in-the-middle attack of a Windows SMB v1-enabled system can become an issue, even if it’s not being used "
However, Uiwix cannot be stopped as of now, the only way to protect yourself is to take some preventive precautions to avoid any trouble in the future. Following these rules strictly may decrease the chances of hijacking by Uiwix -
1. Do not connect your pc, laptop, tablet etc. to a public WiFi hot spot.
2. Do not open any attachments in email from unknown or, suspicious senders.
3. Do not click any links in emails from unknown senders.
4. Do not download any files attached in email from unknown or, suspicious senders.
5. Try to avoid visiting malicious sites.
6. Do not download or, update software/apps from a third-party website, or store.
7. Do not use any out-dated or, pirated software.
8. Install WOT (web of trust) extension, and visit only reputed websites shows by WOT.
9. Keep your antivirus & windows up to date always.
10. You may use Kaspersky anti-ransomware tool, or, Bitdefender anti-ransomware tool for extra security.
11. Disable SMB v1, SMB v2, SMB v3 on windows via registry editing. How to disable it ? Read below.
12. Periodically set restore point. After attack you may able to use System Restore to get back to a known-clean state.
13. Most Important : Always keep offline backup your data, or, do cloud backups.
How to disable SMB v1, SMB v2, SMB v3 on windows via registry editing ?
To enable or disable SMBv1 on the SMB server, configure the following registry key:
Registry subkey: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters
Registry entry: SMB1
REG_DWORD: 0 = Disabled
REG_DWORD: 1 = Enabled
Default: 1 = Enabled
REG_DWORD: 0 = Disabled
REG_DWORD: 1 = Enabled
Default: 1 = Enabled
To enable or disable SMBv2 on the SMB server, configure the following registry key:
Registry subkey:HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\LanmanServer\ParametersRegistry entry: SMB2
REG_DWORD: 0 = Disabled
REG_DWORD: 1 = Enabled
Default: 1 = Enabled
REG_DWORD: 0 = Disabled
REG_DWORD: 1 = Enabled
Default: 1 = Enabled
references :
Tags : Security, Hacks, Ransomware, Malware, Windows, Microsoft, Operating System,
This Post Was Published On My Steemit Blog. Please, navigate to steemit and cast a free upvote to help me if you like my post. First Time heard about Steemit ? Click Here To Know Everything About Steemit










Comments
Post a Comment