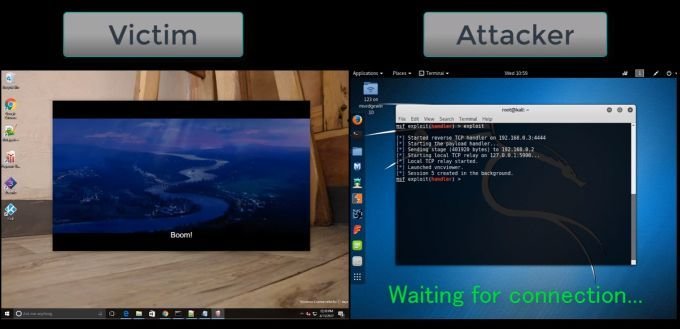
Now-a-days computer and internet is an essential part of our daily life. Everything is now connected to computers through internet. But, in the last couple of years this internet world are being faced numerous cyber attacks & threats. Only a few days ago WannaCry ransomware was spread out in the form of epidemic. Thousands of computers were infected by it. All of this goes to show computer users have to worry about a lot of potential problems these days. Now, another very anxious news is that - "Watching a movie with external subtitles has become a threat right now".
More specifically, researchers came across a vulnerability of how video players load and parse subtitle files. This exploit can lead to computers being taken over by third parties.

Playing a downloaded or copied movie with external subtitles has now turned into an risky habit. All the more particularly, video player software parses and loads subtitles in a certain manner. Along these lines of dealing with subtitles can be misused by hackers who need to pick up remotely control over your PC. It is a significant troubling development, most definitely.
All the more particularly, analysts ran over this vulnerability because of a particular examination. It is feasible for attackers to create malicious subtitle documents which execute malicious code on the victim's gadget. This will just work if the victim plays the video and subtitle document in one of the vulnerable media players. The most noticeably bad part is the manner by which the victim would not know something malicious is going ahead, as the subtitle will show the content in the video player as initially anticipated.

How to protect ?
Please, follow this simple guidelines to keep safe yourself from this kind of attack --
1. Only use reputed video players. There are a numerous types of video player available in the net. But, you only choose reputed video players - VLC Media Player, Kodi, Stremio, and Popcorn time are just a few of the examples. It is possible several other players are susceptible to this malicious subtitle attack as well,
2. Please, update frequently your all installed software including even video players. This will cut off the possibility of being targeted by malicious codes. It is evident this new vulnerability affects millions of computer users all over the world. Most people download a video player and don’t worry about updating it again. This is a very real problem that needs to be addressed.
3. Do not download any subtitles from third party & untrusted repositories. Downloading subtitles from third-party untrusted sources should be avoided at all costs for the time being. Users who stream content legally will not be affected by this problem, though.
4. Please, do not rely on third-party platforms which offer custom subtitles. It is impossible for these platforms to distinguish between legitimate subtitles and those that are embedded with malicious code.
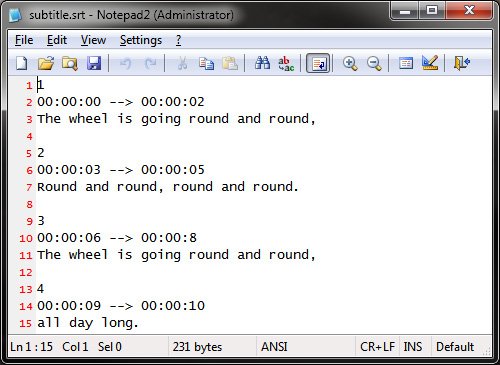
5. Generally all the movie subtitle files are text files. So, you may open this files via notepad to see the content on it. If any malicious codes detected then delete it.
Reference :
Tags : Hacks, Security, Technology, Web, Malware, Movie, Cyber Attack,
This Post Was Published On My Steemit Blog. Please, navigate to steemit and cast a free upvote to help me if you like my post. First Time heard about Steemit ? Click Here To Know Everything About Steemit










Comments
Post a Comment